VLAN is a technology of switched network that provides segmentation on physical LAN and creates logical LAN without connecting end-devices via physical cable.
Characteristics of A simple VLAN configuration:
1. Each VLAN is associated with each subnet and subnet mask2. it is considered a separate logical network.3. layer-3 devices are necessary for communication between two separate VLAN.4. a VLAN creates a logical broadcast domain.
Important benefits of having VLAN:
1. smaller broadcast domains2. improved security3. improved IT efficiency4. Reduced cost5. Better performance6. Simpler project and application management
Table of Contents:
- Tagged and Untagged Ports of VLAN
- VLAN Tagging
- VLAN Tag Field
- Types of VLANs
- Configure a small VLAN network
---------------------------------------------------------------------------------------------------------
Tagged and Untagged Ports of VLAN:
VLAN creation and management are the switch's responsibilities, not end-devices. A configured switch in VLAN has two types of ports, there are access port or untagged port and a trunk port or tagged port.
Access port or Untagged port:
this type of port is associated with only one VLAN id which is configured on the switch port.
1. connected to host devices or end devices.
2. end-devices aren't awarded of VLAN configuration. They send a normal ethernet frame with normal ethernet-header fields.
Trunk port or Tagged port:
It ensures a point-to-point link between two network devices that carry more than one VLAN data/traffic.
1. IEEE 802.1Q protocol is used for designing the trunking system.
2. In the non-cisco world, it is known as a tagged port.
3. trunking can be used between two NICs where 802.1Q is supported.
VLAN Tagging:
The standard Ethernet frame doesn't have a VLAN identification tag, but it must be added when the frame passed through the trunk link. IEEE 802.1Q standards are used for tagging. The VLAN identification tag is about 4 bytes long. It is inserted with the original ethernet frame when passed through the trunk link. The process of traveling different VLAN traffic over the trunk is called trunking. The process of tagging is:
VLAN tag Field details:
When a frame comes from end devices and received by the switch's access port. Then the switch identifies the assigned VLAN ID associated with the access port; the switch inserts the VLAN tag within the original frame and recalculates FCS. After that, if necessary, the frame is sent through the trunk link. So it is important to understand VLAN tag fields.
This VLAN tag consists of 4 fields: Type, User priority, Canonical Format Identifier (CFI), VLAN ID (VID).
User Priority: A 3 bits value field, use to supports service implementation
Canonical Format Identifier (CFI): it enables Token Ring frames to be carried across Ethernet links.
VLAN ID: A 12 bit VLAN identification number, can be up to 4096.
-------------------------------------------------------------------------------------------------------------------------------------------------------
Types of VLANs:
1. Default VLAN: All switch ports are assigned to a VLAN by default named VLAN 1. This VLAN 1 is called the default VLAN. Some important facts about default VLAN:
* it can't be renamed or deleted.
* by default, native and management VLAN are associated with VLAN 1 or default VLAN.
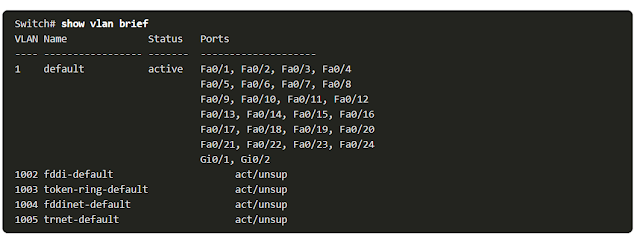
This figure is displaying the outputs of this (#show vlan brief) command. As any other VLANs are not created yet, all ports, native and management VLANs belong to default VLAN 1.
Note: It is considered a security risk if Native and management VLAN belong to default VLAN.
2. Data VLAN: In one word, this VLAN is dedicated to passing user-generated traffic. It can be called a User VLAN as it can make separate network segments or groups of users or devices. A modern network would have many data VLANs depending on their organizational requirements. But Voice and network traffic should not be allowed on data VLANs.
3. Native VLAN: Without VLAN tagging, traffics or data is traveling through the network using native VLAN. VLAN untagging frame can come from legacy devices or can be generated from switches such as the BPDU (Bridge Protocol Data units) frame of STP, DTP, etc. as well as it is useful for VoIP. So the purpose of native VLAN is to help to switch untagged frames in the switched network.
Remember: The Data frame of Native VLAN can traverse the network without VID or VLAN tag.
Key-points about native VLAN:-
- Per trunk per switch configuration
It means, if a switch has four trunk links with the other four switches, every trunk link has an option to set one native VLAN.
- Ensure that Native VLAN is not used anywhere in the network and no port should be assigned to the Native VLAN.
It has a security issue. An attacker can make VLAN double tagging attack. The attacker could embed a hidden 802.1Q tag inside a frame that has already tagged by the native VLAN in front.
- Dropping unexpected data-frame
If a device adds a VLAN tag to native VLAN traffic of another switch. Then if the trunk port of another switch receives a native VLAN tagged frame, the port will drop that frame.
This figure demonstrates the scenario of having Native VLAN mismatch concepts. For this mismatch, the data frame might be dropped unexpectedly.
4. Management VLAN: It is one kind of data VLAN. It is specifically used for network management traffic such as SSH, Telnet, HTTPS, HTTP and SNMP.
5. Voice VLAN: used for voice over IP devices.
------------------------------------------------------------------------------------------------------------------------------
Configure a Small VLAN network:
Suppose there are three data VLAN 10, 20, 30, and one Voice VLAN 40 and 99, 100 are management and native VLAN respectively. We have to make this network working as if every PC can ping other PC correctly.
Commands: Using necessary commands
creation of vlan:
(config)# vlan [vlan-id](config)# name [vlan-name]Note: to create multiple vlan at once;(config)# vlan [vlan-id-range]
Assign ports to a specific vlan:
(config)# interface [interface-id](config-if)# switchport mode accessNote: This command sets the port mode as 'access' statically, On the other hand, Dynamic trunking protocol (DTP) can set port mode automatically.(config-if)# switchport access vlan [vlan-id](config-if)# end
Configure trunk port:
(config)# interface [interface-id](config-if)# switchport mode trunk(config-if)# no shutdown(config-if)# end
Data and voice vlan together:
(config-if)# switchport mode access(config-if)# switchport access vlan 20(config-if)# mls qos trust cos(config-if)# swichport voice vlan 150(config-if)# end
Verification:
# show vlan [brief | id [vlan-id] | name [vlan-name] | summary]# show interface [interface-id] switchport# show interfaces vlan [vlan-id]
Reset:
(privileged)# delete flash:vlan.datNote: vlan.dat is database file located in flash memory in cisco-device to store vlan informations.(privileged)# erase startup-config(privileged)# reload
Note: Always configure both ends of a trunk link with the same native VLAN. If 802.1Q trunk configuration is not the same on both ends, Cisco IOS software reports errors.




0 comments:
Post a Comment